Require work accounts with SSO and Require MFA enhance security for external sharing by requiring your external collaborators to sign-in with single sign-on (SSO) and an additional layer of authentication (Require MFA) to gain access to any content that you share with them.
What's an external collaborator?
An external collaborator is a user who has been invited to collaborate on a sheet or workspace but whose email address doesn’t match the domains associated with the plan that owns the sheet or workspace and who isn’t a member of that plan.
These policies ensure that your external collaborators (users invited from outside your organization's validated domains) use a secure method to log in —and one that passively validates that they're still employed by the organization you intend to collaborate with.
When an external collaborator tries to access an asset that requires SSO/MFA, the user sees a prompt instructing them to log in via SSO. External collaborators must use the Sign in with your company account button to verify their identity using their company’s SSO login. To use SAML/SSO for logging in to Smartsheet, customers on Enterprise plans need to set it up. The configuration can be done at the plan level for Enterprise plan users or at the domain level for all users with a specific email domain.
While Require work accounts with SSO is set up on a plan level, Require MFA can be applied account-wide or to specific workspaces. System Admins can enable Workspace Admins to decide whether to apply the additional security layer to specific workspaces they own.
The policies govern sheets, reports, and dashboards —all items that can be associated with a workspace.
Once enabled, the Require work accounts with SSO and Require MFA policies apply exclusively to core items (sheets, reports, and dashboards) within the core Smartsheet application, excluding items within Smartsheet Premium apps.
Require work accounts with SSO
Require work accounts with SSO is a plan-level policy that guarantees access to Smartsheet is restricted to users with corporate-authenticated login (SSO), thereby reducing the risk of potential unauthorized access.
Supported methods
- Azure work account
- Google work account (ISP domains, i.e., non-work accounts don't work)
- SAML SSO
To use a SAML 2.0 compliant IdP, the external collaborator must be part of an Enterprise plan that has configured a SAML 2.0 Identity Provider for authentication into Smartsheet.
Require MFA
This policy requires external collaborators to authenticate via Multi-Factor Authentication (MFA), enhancing security for them with an additional layer of verification. This ensures that, even if a password is compromised, unauthorized access can be thwarted by the MFA functionality.
If an external collaborator's Identity Provider (IdP) doesn't support MFA or fails to communicate the MFA completion status with Smartsheet, our proprietary email-based MFA serves as a backup.
Supported methods
- SAML (Okta, Azure, AD FS)
- Microsoft work account
Email one-time password
Email-based MFA
This is a one-time, time-limited password mechanism (OTP) provided via email. It's designed to address scenarios where standard MFA through the collaborator's IdP isn't possible.
If the system can't determine that the external collaborator has completed MFA on an asset where the policy applies, an email is sent to their account as soon as they click on the asset.
If the user enters the verification code incorrectly three consecutive times, they must wait 30 minutes to try again.
About the mobile app
The Smartsheet mobile app honors any Secure External Access policies enabled in the Admin Center, just like the web and desktop apps.
System Admins
To activate the Require work accounts with SSO policy:
- Go to the Admin Center.
- Select the menu icon and navigate to Settings > Secure External Access.
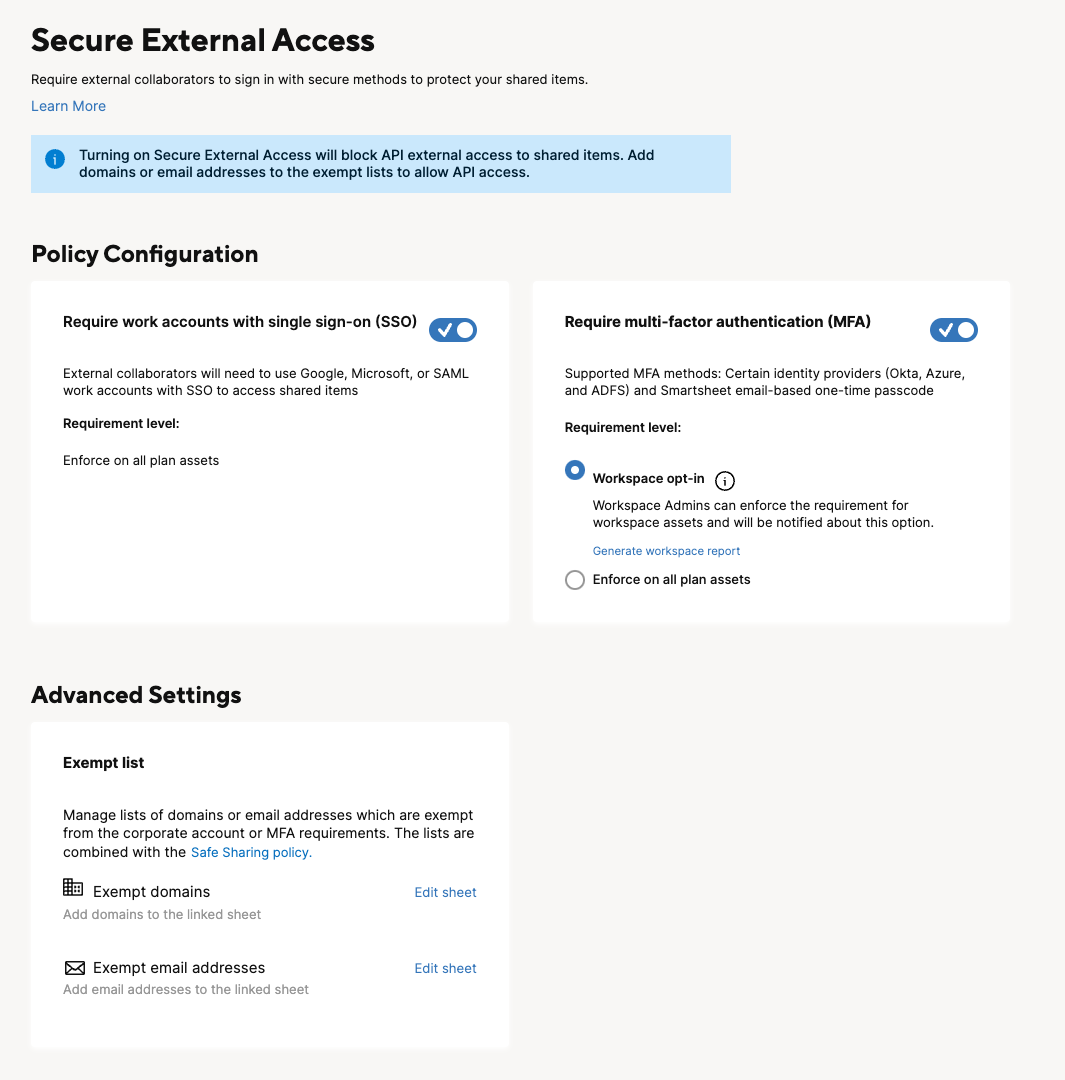
Slide the Require work accounts with single sign-on (SSO) toggle to turn on the policy.
If the internal sign-in option doesn't have SSO enabled, the Require work accounts with SSO policy will be automatically disabled.
To activate the Require MFA policy:
- Go to the Admin Center.
- Select the menu icon and navigate to Settings > Secure External Access.
- Slide the Require MFA toggle to turn on the policy.
- To allow Workspace Admins to apply the policy on specific workspaces, select the Workspace opt-in button.
- To enforce the policy on all plan assets, select Enforce on all plan assets.
Workspace Admins
- Workspace Admins can't set up the plan-level Require work accounts with SSO policy. The configuration is required by a System Admin.
- If a System Admin enables Workspace opt-in, Workspace Admins can enforce the Require MFA policy on specific workspaces.
To generate a report showing all the workspaces with the Require MFA policy enforced, select Generate opt-in report. The workspace report spreadsheet includes the workspace name, indicating whether the Require MFA policy applies to each workspace, along with a URL link to access it, and a list of users with Admin permissions on the workspace.
You can also use the public sheet API to access this report and track its sheet ID.
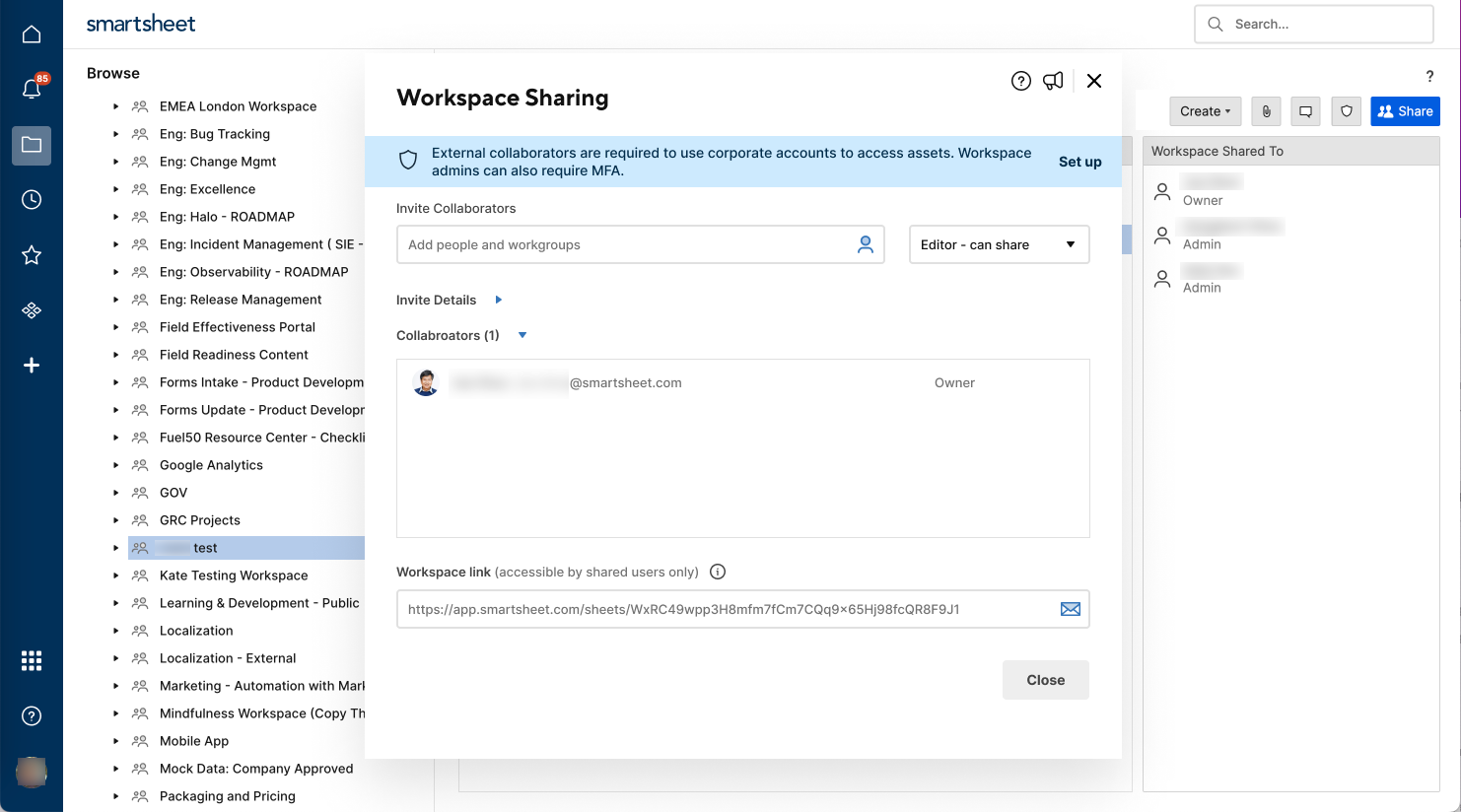
To activate MFA for workspace access:
- Go to the workspace and select Share in the top right corner.
- Select Set up from the top of the sharing window.
- Slide the Require MFA toggle to turn on the feature. Settings apply to all items in the workspace, not to individual items.
Exempt list
The Exempt list (also known as the Trusted Domain list) allows System Admins to specify domains and individual email addresses that are exempt from the policies.
Enabling an exempt list initiates the creation of a sheet with specific columns. All System Admins have access to this sheet.
To create an Exempt list:
- Go to Admin Center.
- Select the menu icon and navigate to Settings > Secure External Access.
- Under Advanced Settings, select Create sheet on either of the following:
- Exempt domains
- Exempt email addresses
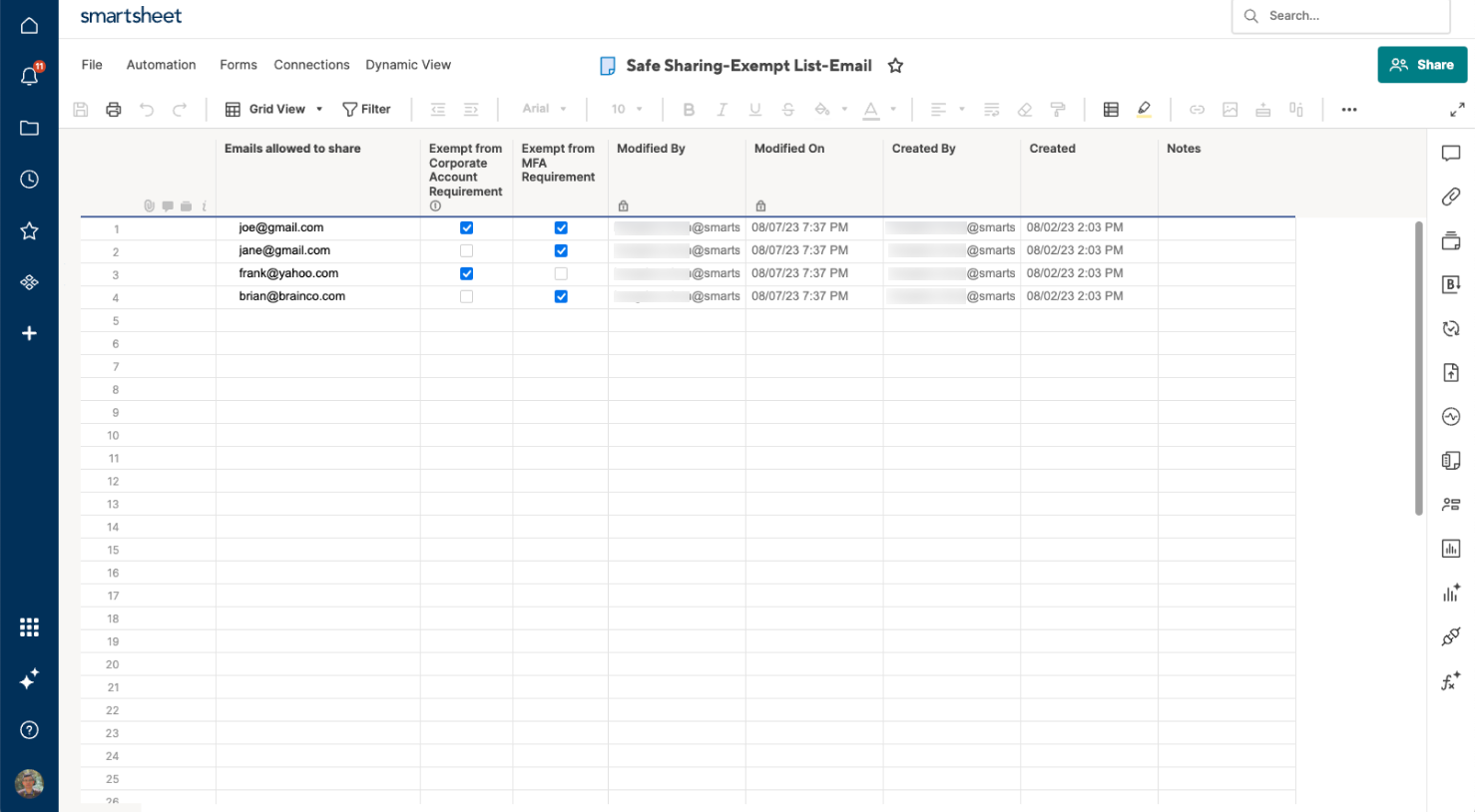
- To add new domains or email addresses to the Exempt list, enter them in the Domains/Emails allowed to share column and use the checkbox columns to indicate if the entity is exempt from the policies.
Exempt list sheet
System Admins can only add, edit, and delete rows on the sheet. The sheet contains the following columns:
| Column name | Description |
|---|---|
| Column name Domains/Emails allowed to share | Description Lists the domain/email address that are allowed to share content with. |
| Column name Exempt from Corporate Account Requirement | Description A checkbox that, when marked, exempts the domain/email address from requiring corporate account login to access shared content. |
| Column name Exempt from MFA Requirement | Description A checkbox that, when marked, exempts the domain/email address from the requirement to use MFA for accessing shared content. |
| Column name Modified By | Description Indicates the last user who made changes to the row, providing accountability and tracking for updates. |
| Column name Modified On | Description Shows the date and time when the last modification was made to the row, helping to maintain a timeline of changes. |
| Column name Created By | Description Identifies the user who originally created the entry in the sheet, establishing the origin of the data. |
| Column name Created | Description Displays the date and time when the entry was created, giving a historical context. |
| Column name Notes | Description An open field for any additional information, comments, or rationale behind the domain/email address status. |
API calls
External collaborators using public API calls to access shared Smartsheet assets that are protected by Require work accounts with SSO or Require MFA policies can only gain access to those assets via Smartsheet API if their domain or email address is on the Exempt list, or if it's a validated domain of the plan.
If your external collaborators encounter issues accessing their shared assets, they should reach out to the System Admin of the plan to which those assets belong.
Other things to know
- These policies apply to users who aren't part of any validated domain in the plan that enabled the policy, or any domain/email address mentioned in the Exempt list for these policies.
- Issued OTPs have a lifespan of ten minutes. Post-expiration, users must generate a new one.
- Existing System Admins are responsible for granting access to the Exempt list sheet to new or future System Admins.
- Updates (new exemption entries) to the Exempt list may take up to three minutes to apply.
Can we disable the email-based MFA functionality once the Require MFA policy is enabled?
No. Once the Require MFA policy is active, System Admins can't disable the email-based MFA functionality. It's designed as a backup to ensure continued security even if the primary MFA method is unavailable.
How will external collaborators who aren't part of any organization with Require work accounts with SSO/Require MFA access the system? Especially those who are independent consultants?
- External collaborators must use their work email or a corporate login account set up with Google or Microsoft SSO.
- They can receive an email-based code (email-based MFA) for verification.
- System Admins can add users to the Exemption list if necessary.
Will any Workspace Admin be able to implement these policies?
Workspace Admins can enable the Require MFA policy at workspace level if a System Admin has enabled Require MFA policy at workspace level. Workspace Admins can't configure the Require work accounts with SSO policy.
Are there any domains automatically added to the Exempt list?
Yes. All verified domains within the plan are automatically exempted from both the Require work accounts with SSO and Require MFA policies, as users from these domains are treated as internal users to the plan.

